Hardware Protection through Obfuscation: Forte, Domenic, Bhunia, Swarup, Tehranipoor, Mark M.: 9783319840680: Amazon.com: Books

PDF) Hardware Obfuscation Driven by QR Pattern using High Level Transformations | WARSE The World Academy of Research in Science and Engineering - Academia.edu
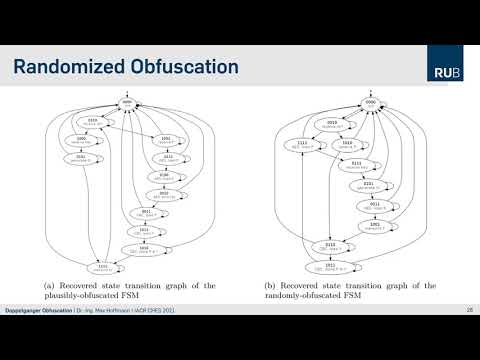
Paper: Doppelganger Obfuscation — Exploring theDefensive and Offensive Aspects of Hardware Camouflaging

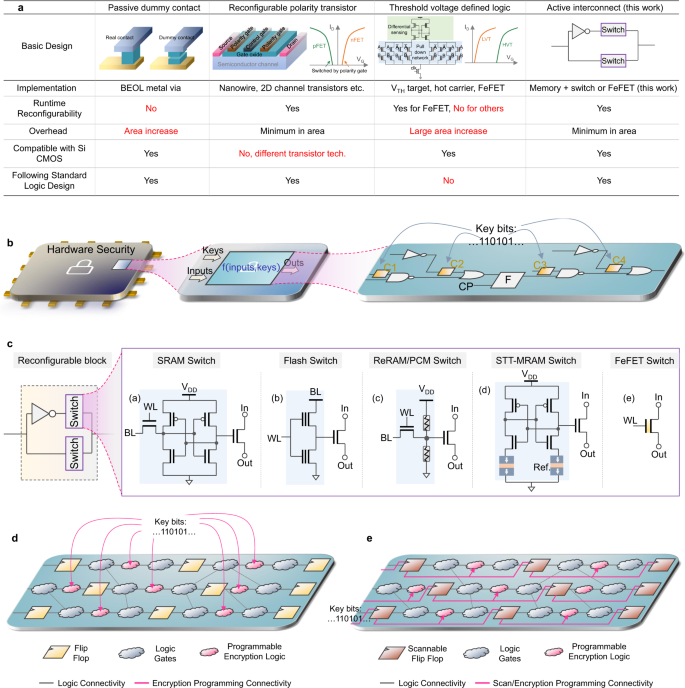
SAIL: Machine Learning Guided Structural Analysis Attack on Hardware Obfuscation – CAD for Assurance