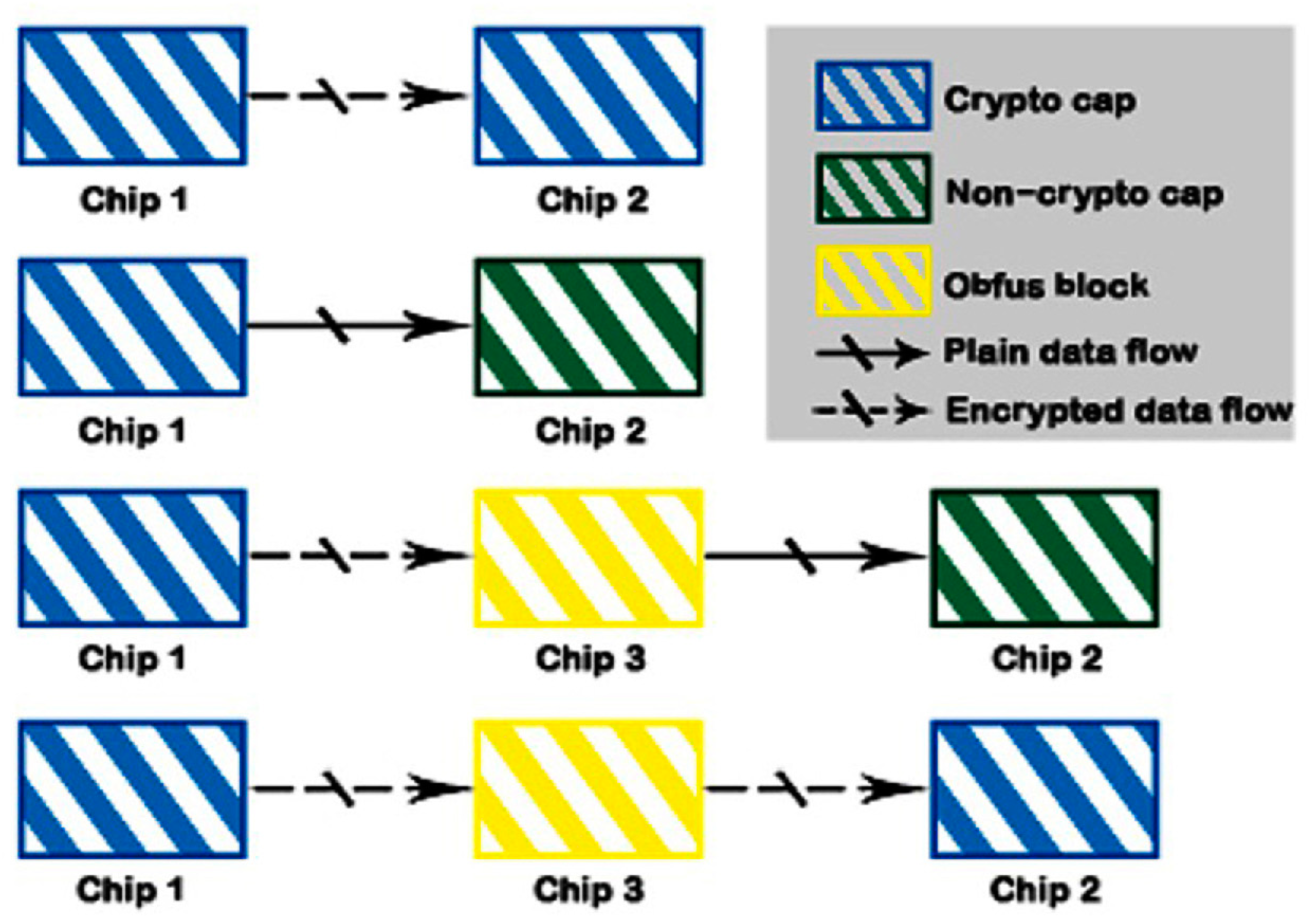
Information | Free Full-Text | FPGA-Based Voice Encryption Equipment under the Analog Voice Communication Channel

Integral 64GB Courier-197 256-Bit USB Stick verschlüsselt - USB Stick Passwort geschützt - FIPS 197 zertifiziert, Schutz vor Brute-Force-Angriffen & Super USB3.0 Übertragungsgeschwindigkeiten: Amazon.de: Computer & Zubehör

How Does Hardware-Based SSD Encryption Work? Software vs Hardware, AES 256-bit and TCG Opal 2.0 - Kingston Technology

Energy-efficient encryption for the internet of things | MIT News | Massachusetts Institute of Technology

Cabel on Twitter: "⑤ Security. This new chip means storage encryption keys pass from the secure enclave to the hardware encryption engine in-chip — your key never leaves the chip. And, they

Buy Widenbit Encrypted USB Flash Drive, with Level Encryption Chip,AES 256-Bit Hardware Encryption, for Data Security.(Creative Business Gift) Online at desertcartFiji