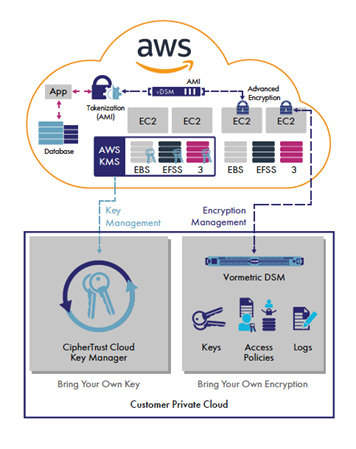
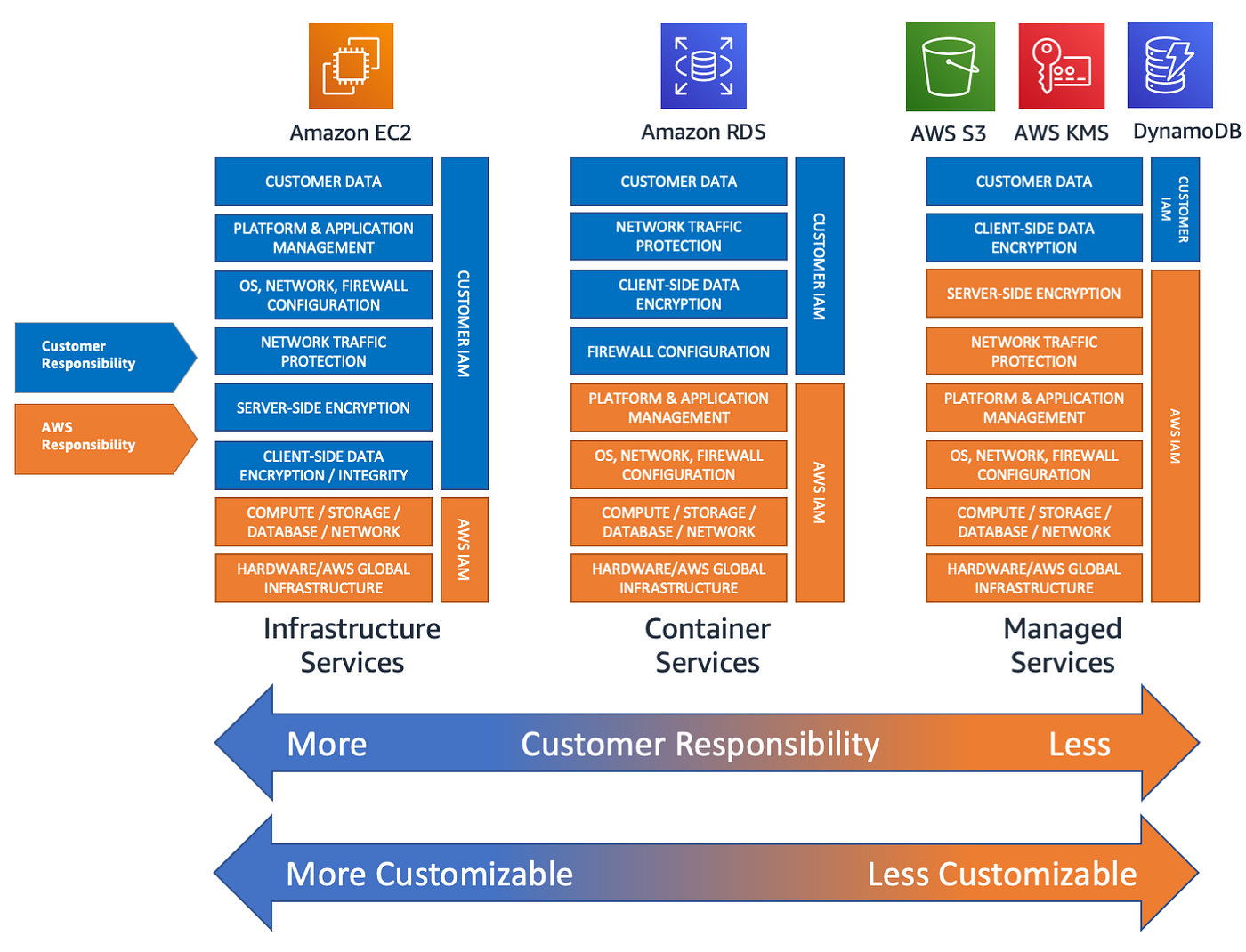
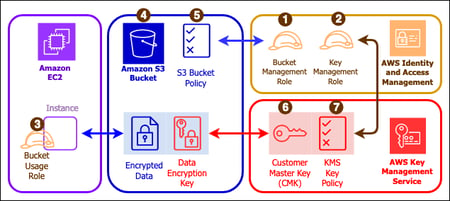
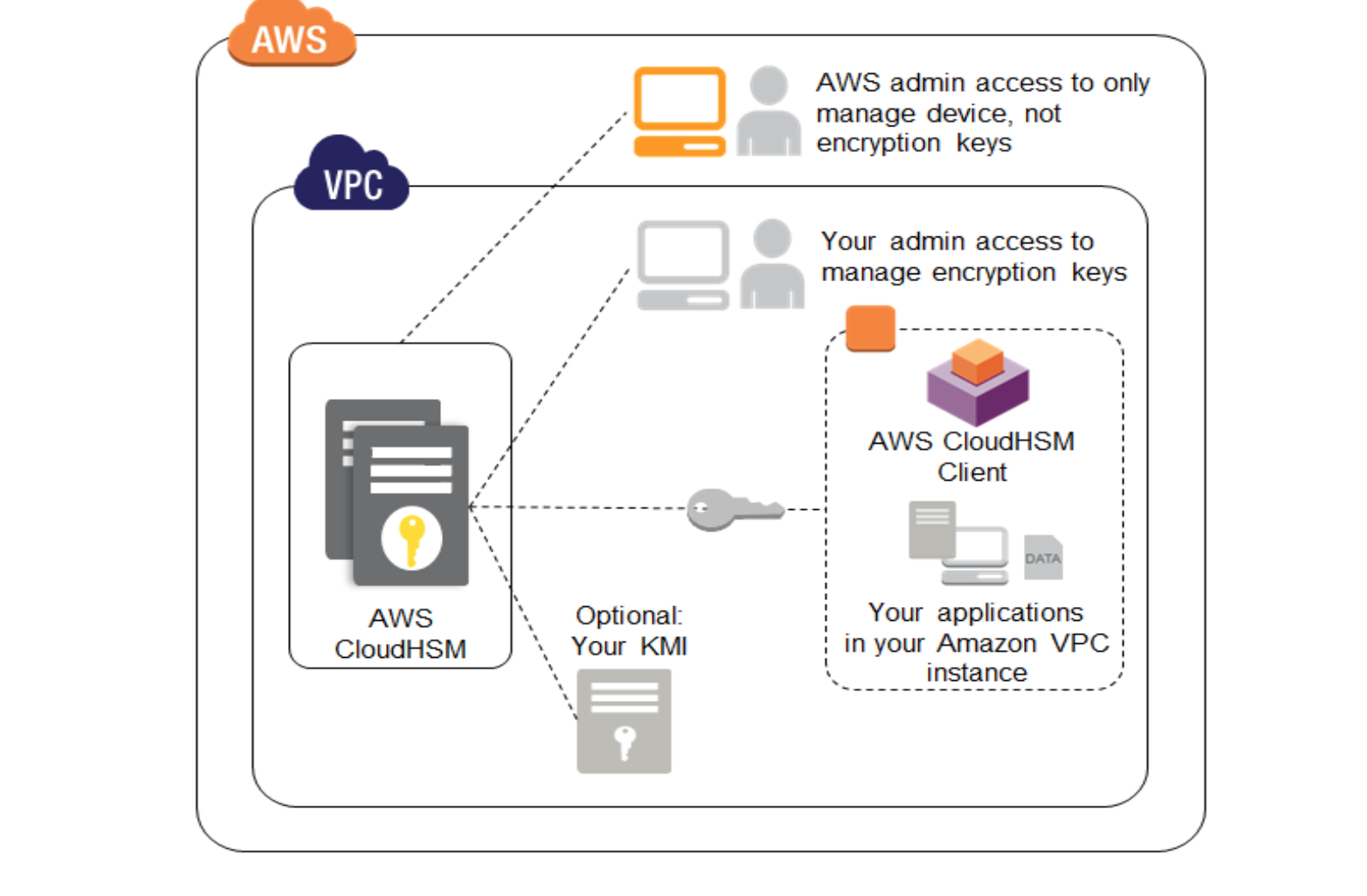
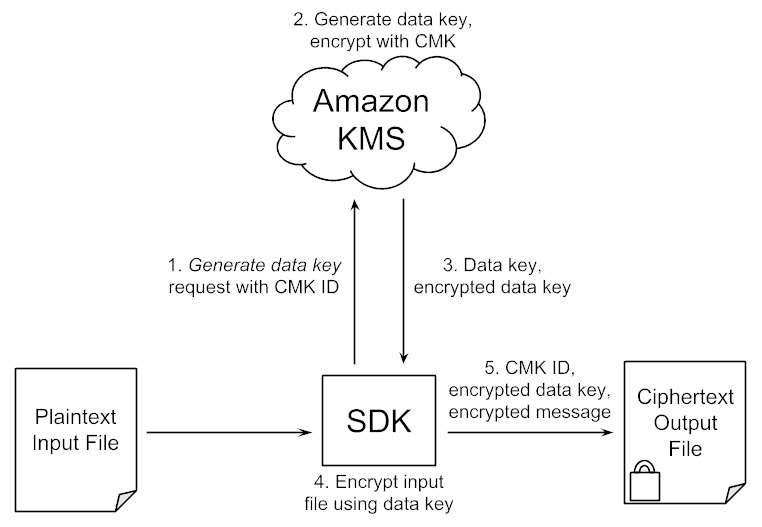
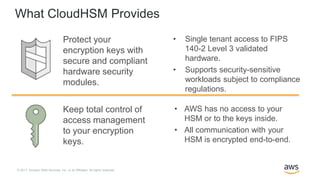
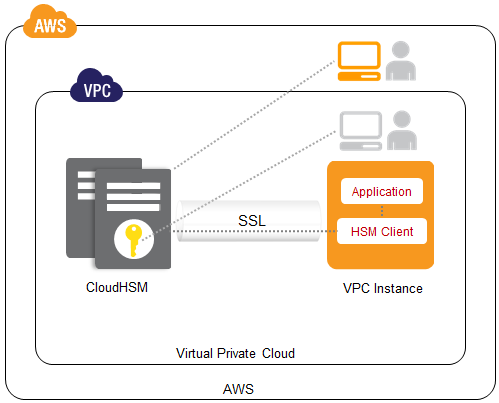
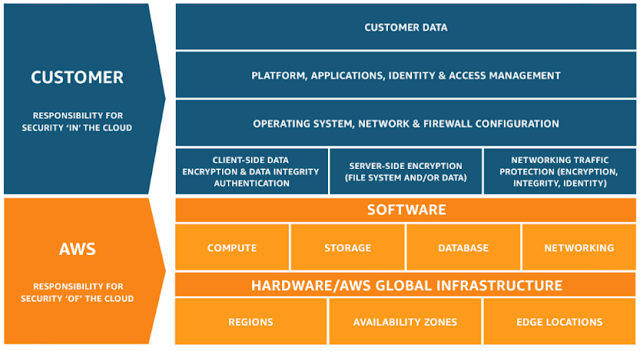
Demystifying KMS keys operations, bring your own key (BYOK), custom key store, and ciphertext portability | AWS Security Blog
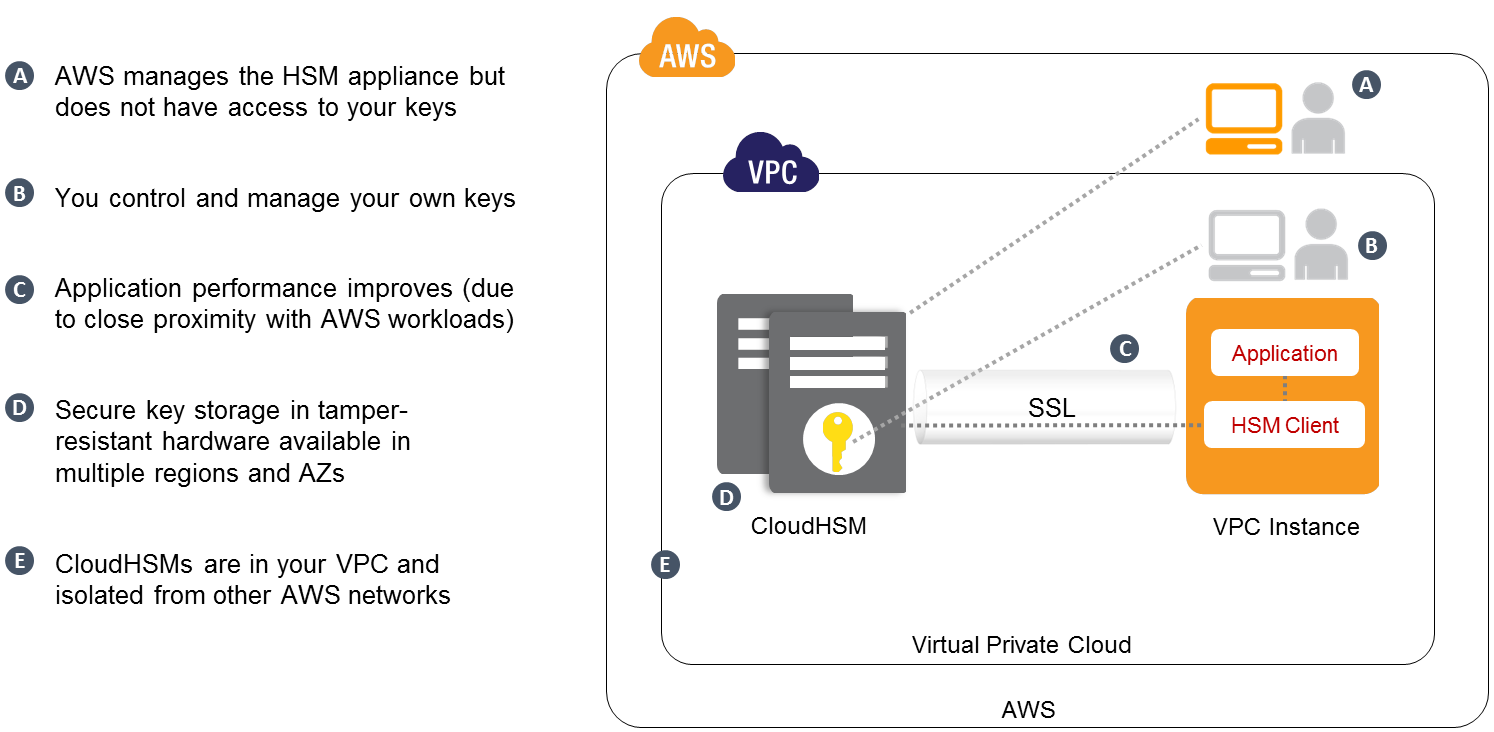
Amazon Web Services Launches CloudHSM, A Dedicated Hardware Security Appliance For Managing Cryptographic Keys | TechCrunch